TrustZero

Enterprise-Level Continuous Validation
Organizations that rely on high-assurance physical access control systems (PACS) to help protect their facilities from unauthorized access need robust validation systems. Given the number and types of certificate issuers within a given trust community, the validation process is quite complex, especially in a community like the Federal Public Key Infrastructure (FPKI).
Unfortunately, some client and server operating system validation processes are not 100% reliable. They do not always communicate effectively with each other, authentication servers, or certification authorities (CAs) and their protocols are difficult or impossible to understand. It’s like playing a game of operator with two cans and a fraying string while trying to figure out whether to let someone into a facility.
The Solution
During a decade of testing and certifying FIPS 201-compliant products for the federal government’s Federal Identity, Credential, and Access Management (FICAM) program, CertiPath noticed deficiencies in the models that the first generation of validation systems were built on. Those observations, coupled with CertiPath’s extensive PACS experience, cloud experience, and the PKI expertise it leverages to run the CertiPath Bridge CA, prompted the company to develop a validation system solution for high-assurance PACS.
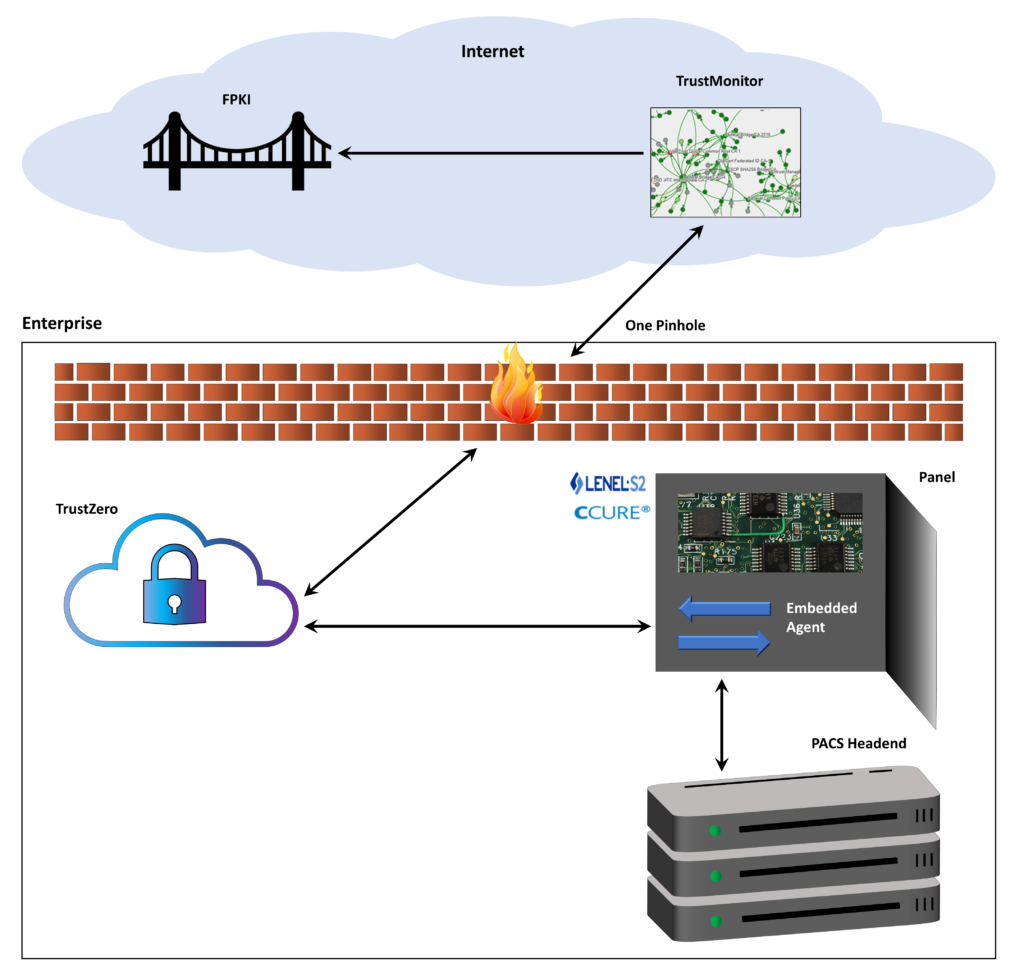
Backed by continuous monitoring, TrustZero is a cloud-based tool that provides enterprise-level continuous validation for PACS. It works in conjunction with CertiPath’s popular TrustMonitor® credential validation platform, which performs 24/7 monitoring for the PKI trust fabric. Whether an organization has one PACS or several, TrustZero provides a single network location to respond to all validation queries for all credentials within a trust federation.
When paired with TrustMonitor Enterprise, TrustZero can provide this same validation for credentials issued by local trust CAs for intranets, internal networks, VPNs, non-person entities, Internet of Things (IoT) devices, and other items that are issued certificates from private CAs.
Regardless of the number and type of certificate-bearing items presented for PACS authentication, TrustZero consolidates all validation responses as a service. Whether an organization needs to validate credentials from a public CA, a private CA, or both public and private CAs, TrustZero handles them all.
Cloud Based, Secure, and a Whole Lot More
In the federal sector there’s an impetus to move validation off site, even for on-premises applications like PACS. As mandated in Executive Order (EO) 14028, “Improving the Nation’s Cybersecurity,” civilian agencies must adopt cloud technology and Zero Trust Architecture. Per EO 14028, the Zero Trust security model “requires continuous verification of the operational picture via real-time information from multiple sources to determine access and other system responses.” Cloud-powered TrustZero helps satisfy those requirements by communicating with every CA and checking its Certificate Revocation List (CRL) every 60 seconds. That’s as close to real time as you can get.
TrustZero complies with:
- HSPD-12
- FIPS 201
- Federal Common Certificate Policy
- PKIX Path Building
- EO 14028/OMB 22-09/Zero Trust
Configuration Options Enhance Value
TrustZero can be configured to support a variety of business logic use cases.
 VIP Setting
VIP Setting
The VIP setting enables an organization to more finely tune validation to suit its risk tolerance level for certain populations (e.g., directors, executives, etc.) as may be appropriate for any given facility’s security posture. This feature allows the organization to apply a business rule that says, “For a particular subset of all persons, based on criteria exhibited in the user’s record or credential, TrustZero will validate a credential even if it would otherwise be invalid.” There are guardrails for this feature. Not all invalid card conditions are likely to still be acceptable to an organization. For example, a credential that expired within the past 24 hours is of much lower risk than a credential that was reported stolen and revoked. The VIP feature evaluates who should be given access and under what conditions, creating a powerful way to automate exception processing that would otherwise occur in practice but would go unlogged. TrustZero lets an organization facilitate normal lobby behavior but with awareness of exceptions as they occur and the ability to notify security personnel so they can help VIPs more seamlessly get their credentials back to a valid state.
 Extended Validity Period
Extended Validity Period
The Extended Validity setting enables an organization to increase the amount of time a credential’s status is considered valid. Extended Validity begins when TrustZero receives no response during a TrustMonitor validity interval check, such as during a wide area network outage. If TrustZero receives an “Invalid: Unknown” or “Invalid: Unavailable” response from TrustMonitor for a credential that was valid at the previous interval check, during the Extended Validity Period TrustZero continues to communicate the credential status as “Valid” for the amount of time configured in the setting. If the credential status remains “Invalid: Unknown” or “Invalid: Unavailable” when the Extended Validity Period expires, TrustZero communicates the credential as “Invalid.”
 Degraded Mode
Degraded Mode
What happens when you cannot get validity information for everyone in your PACS? Degraded Mode allows an organization to continue operations during a widespread network or validation outage. It is consistent with the U.S. government FICAM standard that stipulates that a system shouldn’t deny access to known cardholders in the event of a network outage and should continue to operate at last know status for a defined time for which an organization is willing to accept risk. When Degraded Mode is enabled, TrustZero communicates all credentials with a status of “Invalid: Unknown” or “Invalid: Unavailable” as “Valid” and it communicates all credentials with an “Invalid: Revoked” or “Invalid: Certificate Expired” status as “Invalid.”