Federated Trust
INTRODUCTION TO FEDERATED TRUST
The CertiPath Public Key Infrastructure (PKI) Bridge enables cross-organizational trust for its members, who operate high-assurance identity credentialing systems known as enterprise PKI. Several members provide Personal Identity Verification-Interoperable (PIV-I) credentials to other organizations. This bridged trust is characterized by a hub-spoke peer-to-peer environment in which all members retain control over their individual trust domain policies and technical solutions but agree to a common set of overarching requirements embodied in federated trust. Each member establishes parity with the federated trust's requirements, which in turn enables the trust between members.
Federated trust offers a secure and efficient means of exchanging information. It eliminates the costly and complex process of individually mapping PKI/hardware tokens and issuing project-specific credentials for every new customer, supplier, or partner.
As an alternative, for those organizations not interested in maintaining a distinct trust domain, CertiPath provides the option of electing to adopt the CertiPath policy and subordinating under the CertiPath Root. In this scenario, the member organization must operate its identity credentialing system in accordance with CertiPath’s policies.
CertiPath’s trust community extends beyond its own enterprise members to the U.S. federal government via a bridge-to-bridge trust relationship between CertiPath and the U.S. Federal Bridge, which operates its own hub-spoke peer-to-peer environment for the U.S. federal agencies. This hub-to-hub relationship enables inter-organizational trust between the members of the two bridges.
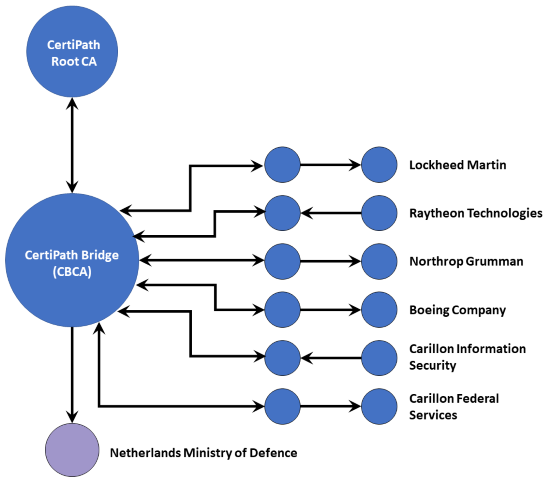
CertiPath extends to commercial entities the same trust fabric that the Department of Defense and federal agencies rely on. CertiPath provides SHA2 support at the Medium Software, Medium Hardware, High Hardware, and IceCAP (PIV-I) levels of assurance through federated trust.

FEDERATED TRUST
> Trust Community
> Policy Management Authority
> Become a Member
PHYSICAL ACCESS
> ICAM ProofCards
The CertiPath high-assurance trust environment is governed by the CertiPath Policy Management Authority (PMA), a member-driven committee chaired by CertiPath.

SYSTEM DESIGN SERVICES
> Overview
The table on the Becoming a Member page lists expectations for an organization joining the CertiPath community as either a member of the CertiPath hierarchy subordinated to the CertiPath Root CA or as an enterprise PKI in a peer-to-peer relationship with federated trust.
